What is Tinytag DI?
Tinytag DI is the secure data logging software for Tinytag data loggers. Manage and monitor who has access to your data loggers and what they can do with them, review activity history in the audit log and maintain accurate, traceable and reliable data in a closed, secure data logging system. In regulated industries where rigorous digital record-keeping is paramount, Tinytag DI can aid compliance with data governance standards.
How it Works

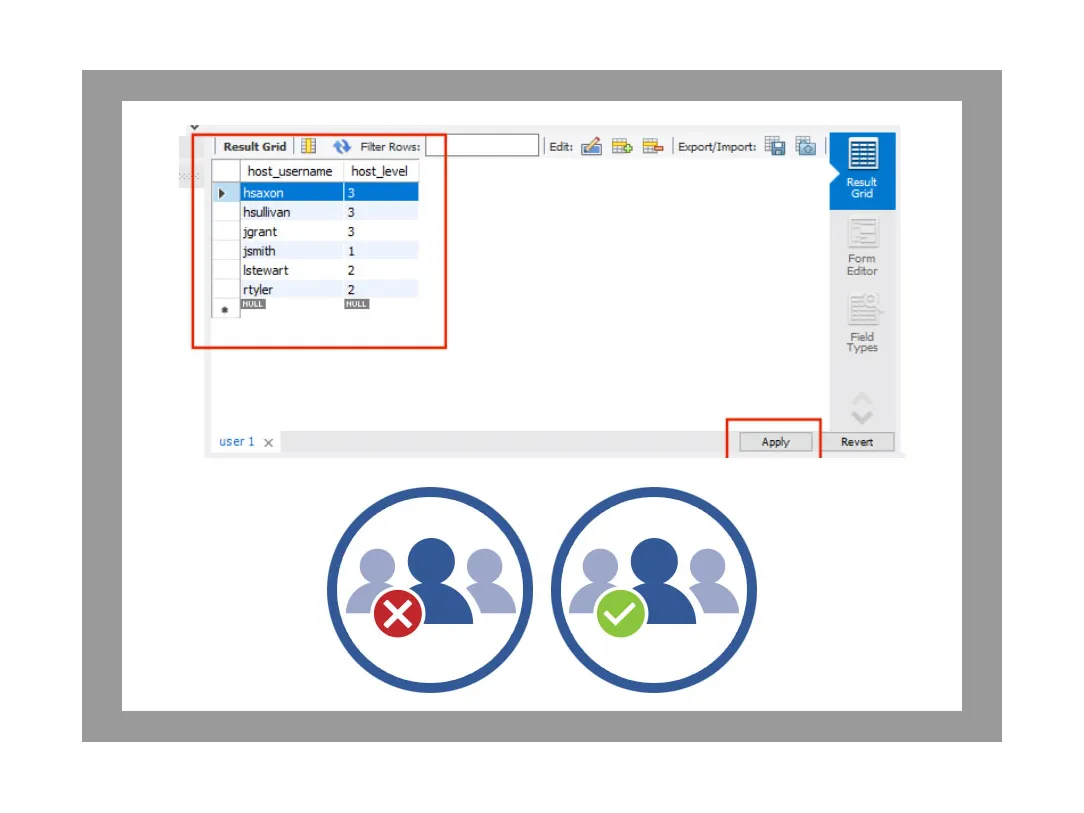
1. Authorised users only. Users are registered in the system against their Windows-OS login. Unauthorised users cannot access the system or data loggers.

2. User activity is controlled. Registered users are given an access level appropriate to their role within the organisation. This controls what users can do with data loggers.

3. User access to data is restricted. Data loggers are assigned to users, individually or in groups, to control which data loggers users have access to.

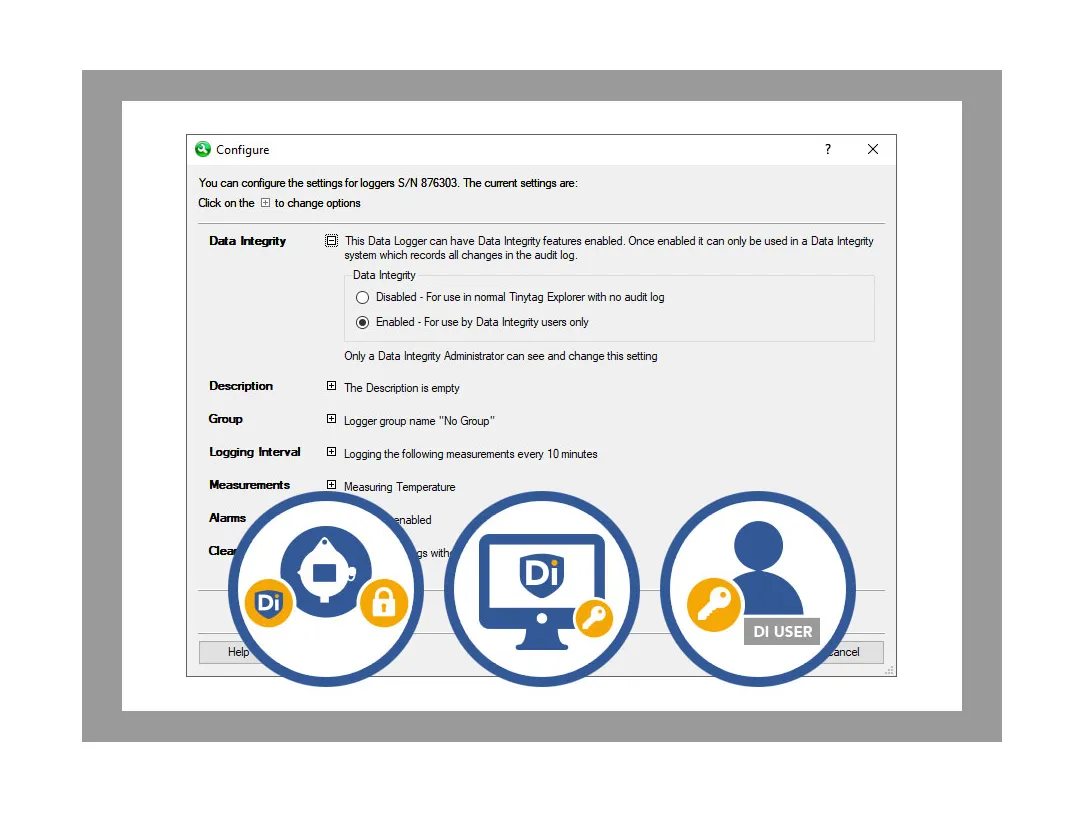
4. Closed system protects data. Administrators enable data integrity features on data loggers, making them part of the closed system. They cannot be accessed by unauthorised users or on other systems.
Features
Tinytag DI combines the features of Tinytag Explorer and Tinytag Explorer Connect with practical data security controls that help you to protect your data.
Closed System
Safeguard your critical data in a closed, secure system.
- Add data integrity features to any data logger at any time.
- Lock data loggers to your Tinytag DI system.
- Restrict access to authorised users only.
User authentication
Control access to your data logging system
- Registered users are verified every time they access the system.
- Changes are attributable to individual users.
- Keep data safe from unintended or intentional manipulation.
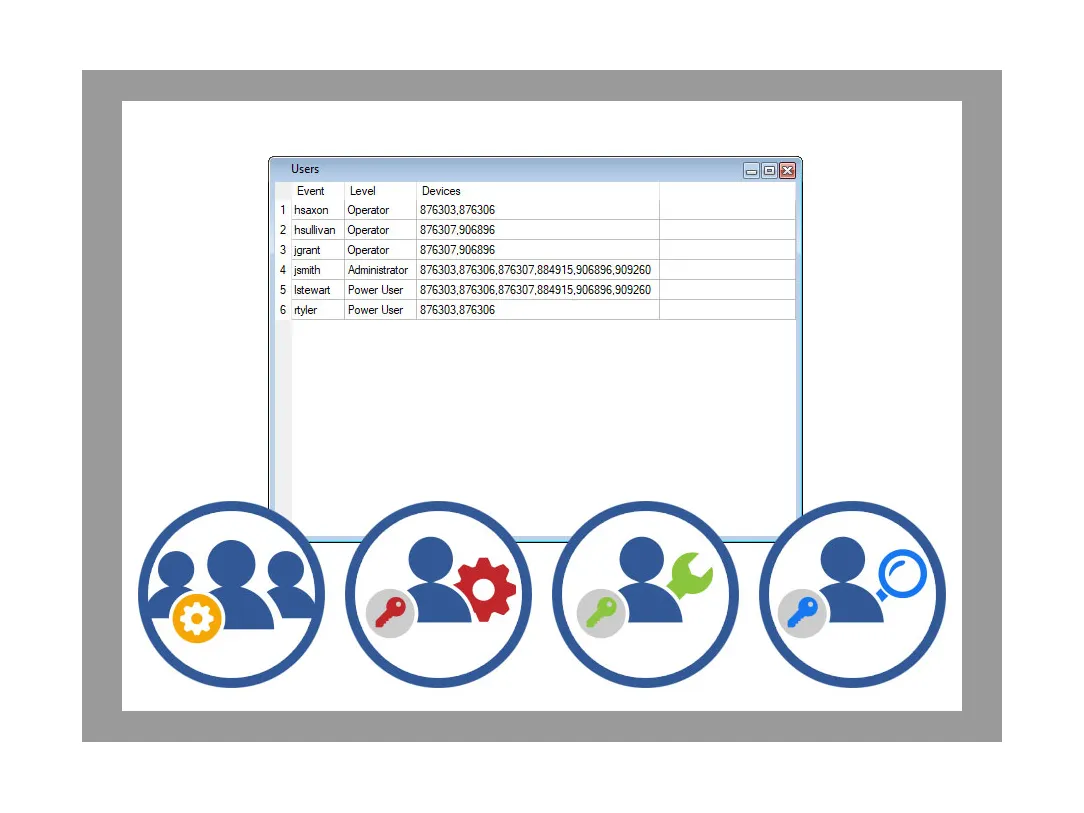
User access levels
- Administrator: users who can view/configure all data loggers, access audit logs and enable/disable data integrity features on data loggers.
- Power User: users who can view/configure the data loggers assigned to them and access audit logs.
- Operator: 'read-only' users who can view data from data loggers assigned to them.
Groups
Control user access to data loggers
- Assign access to data loggers individually or in bulk.
- Users can only view data loggers that are assigned to them.
- Set up Groups according to location, department or other organisational needs.
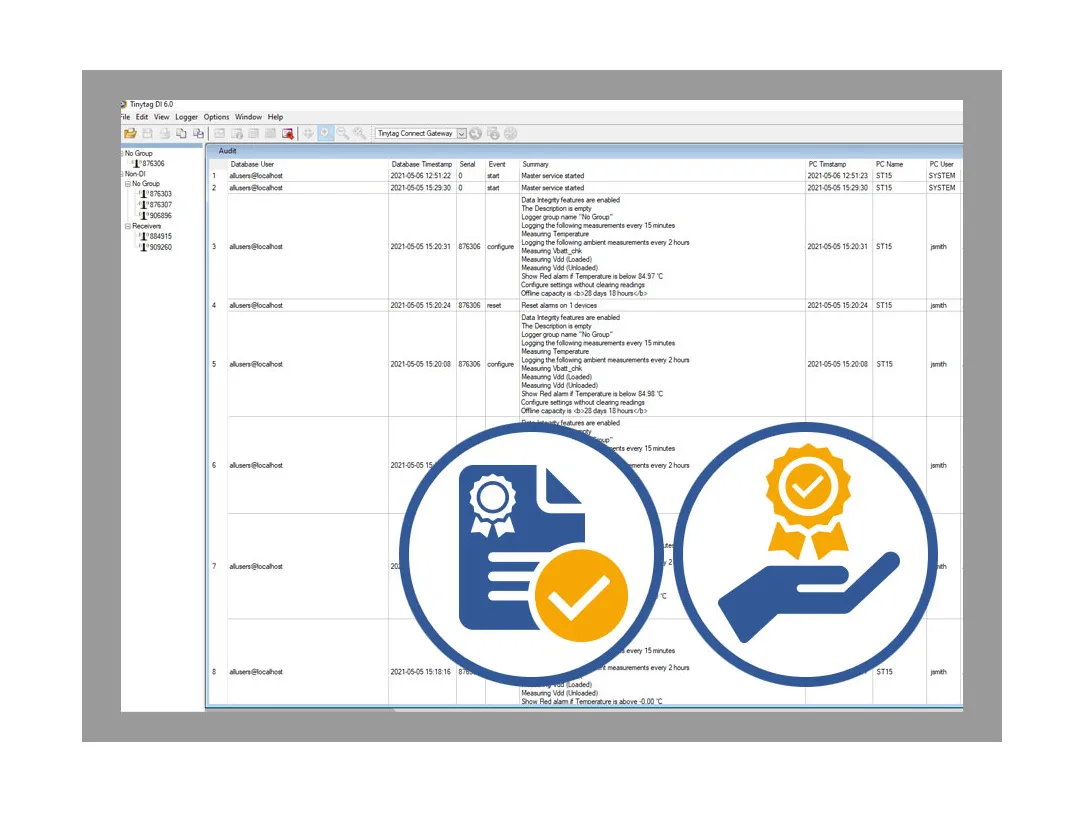
Audit logs
Ensure the accuracy and consistency of your data.
- Records key changes made to a data logger's configuration and system-critical events e.g. alarms.
- Events are dated, time-stamped and attributed to users, PCs and data loggers.
- Enables full reconstruction of data history.